安卓 7 之前把 CA 证书安装到用户证书下即可, 但在安卓 7 以上系统中, 由于默认只信任系统级证书 (APP 可以设置信任范围, 默认仅信任系统范围的证书), 为了正常抓包, 需要将 CA 证书安装到系统证书目录。
准备条件
- 一台已 root 的安卓手机
- 电脑安装 Charles 抓包工具 (其他抓包工具也是一样的原理)
- 电脑安装 ADB (Android Debug Bridge)
获取 Charles 根证书
导出证书文件
在 Charles 中导出证书 (.pem 格式), 命名为 charles.pem
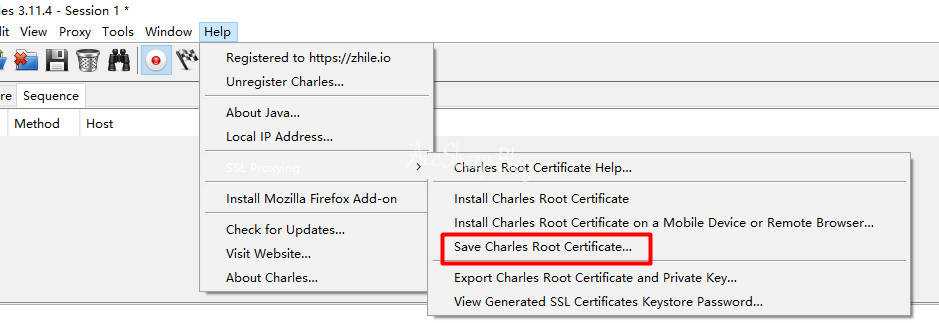
获取证书文件名
在证书所在路径打开命令行, 执行以下命令
openssl x509 -inform PEM -subject_hash_old -in charles.pem
示例输出
faf57fe3
-----BEGIN CERTIFICATE-----
MIIFMDCCBBigAwIBAgIGAXWqowQPMA0GCSqGSIb3DQEBCwUAMIGbMSwwKgYDVQQD
...
aXDrm30UE6+dWdQ3n0ePVLNcHV+ZrIqwka94M/t8HavZpm4y
-----END CERTIFICATE-----
然后将 charles.pem 重命名为 faf57fe3.0 (faf57fe3 需根据实际生成结果调整)
编辑证书内容
使用命令获取证书扩展内容, 如果没有这一步安装的证书没有详细信息
openssl x509 -inform PEM -in faf57fe3.0 -noout -text
输出示例包含证书详细信息, 将其复制并粘贴到证书结尾, 组合为完整的 CA 文件。保存为 UTF-8 编码, 换行符设置为 LF
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
01:76:ee:04:af:62
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = "Charles Proxy CA (11 Jan 2021, ACESHEEP)", OU = https://charlesproxy.com/ssl, O = XK72 Ltd, L = Auckland, ST = Auckland, C = NZ
Validity
Not Before: Jan 9 20:37:33 2021 GMT
Not After : Jan 9 20:37:33 2022 GMT
Subject: CN = "Charles Proxy CA (11 Jan 2021, ACESHEEP)", OU = https://charlesproxy.com/ssl, O = XK72 Ltd, L = Auckland, ST = Auckland, C = NZ
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:a1:02:b1:62:11:c1:4d:f3:3f:2d:71:b8:e4:26:
....
b0:fc:24:e5:c6:d9:cd:09:01:a8:8f:d4:8e:10:b8:
23:9b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints: critical
CA:TRUE
Netscape Comment:
....This Root certificate was generated by Charles Proxy for SSL Proxying. If this certificate is part of a certificate chain, this means that you're browsing through Charles Proxy with SSL Proxying enabled for this website. Please see http://charlesproxy.com/ssl for more information.
X509v3 Key Usage: critical
Certificate Sign
X509v3 Subject Key Identifier:
94:88:6E:5E:E4:17
Signature Algorithm: sha256WithRSAEncryption
8a:e4:47:c4:f2:ba:07:46:08:03:0c:91:94:c9:cf:b4:9c:73:
....
ae:39:f3:a2
组合后的完整文件内容
# cat faf57fe3.0
-----BEGIN CERTIFICATE-----
MIIFPjCCBCagAwIBAgIGAXbuBK9iMA0GCSqGSIb3DQEBCwUAMIGjMTQwMgYDVQQD
....
86I=
-----END CERTIFICATE-----
Certificate:
Data:
Version: 3 (0x2)
Serial Number:
01:76:ee:04:af:62
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN = "Charles Proxy CA (11 Jan 2021, ACESHEEP)", OU = https://charlesproxy.com/ssl, O = XK72 Ltd, L = Auckland, ST = Auckland, C = NZ
Validity
Not Before: Jan 9 20:37:33 2021 GMT
Not After : Jan 9 20:37:33 2022 GMT
Subject: CN = "Charles Proxy CA (11 Jan 2021, ACESHEEP)", OU = https://charlesproxy.com/ssl, O = XK72 Ltd, L = Auckland, ST = Auckland, C = NZ
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:a1:02:b1:62:11:c1:4d:f3:3f:2d:71:b8:e4:26:
....
b0:fc:24:e5:c6:d9:cd:09:01:a8:8f:d4:8e:10:b8:
23:9b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints: critical
CA:TRUE
Netscape Comment:
....This Root certificate was generated by Charles Proxy for SSL Proxying. If this certificate is part of a certificate chain, this means that you're browsing through Charles Proxy with SSL Proxying enabled for this website. Please see http://charlesproxy.com/ssl for more information.
X509v3 Key Usage: critical
Certificate Sign
X509v3 Subject Key Identifier:
94:88:6E:5E:E4:17
Signature Algorithm: sha256WithRSAEncryption
8a:e4:47:c4:f2:ba:07:46:08:03:0c:91:94:c9:cf:b4:9c:73:
....
ae:39:f3:a2
这样组合好后就可以进行下一步了
导入到安卓手机
按照以下步骤将证书导入到 /system/etc/security/cacerts/
关闭验证
adb root
restarting adbd as root
adb disable-verity
using overlayfs
Successfully disabled verity
Now reboot your device for settings to take effect
adb reboot
OTA 升级需要开启验证
adb root
restarting adbd as root
adb enable-verity
Successfully enabled verity
Now reboot your device for settings to take effect
adb reboot
将证书移动到系统目录
开发版系统自带 root 的情况
# 第一个窗口
adb root
adb shell
su
mount -o rw,remount /system
# 打开第二个窗口上传证书
adb push faf57fe3.0 /system/etc/security/cacerts/
# 第二个窗口传完证书继续执行
chmod 644 /system/etc/security/cacerts/faf57fe3.0
reboot
使用 Magisk (面具) root
adb push faf57fe3.0 /sdcard/
adb shell
su
mount -o rw,remount /system
mv /sdcard/faf57fe3.0 /system/etc/security/cacerts/
chmod 644 /system/etc/security/cacerts/faf57fe3.0
reboot
验证证书是否安装成功
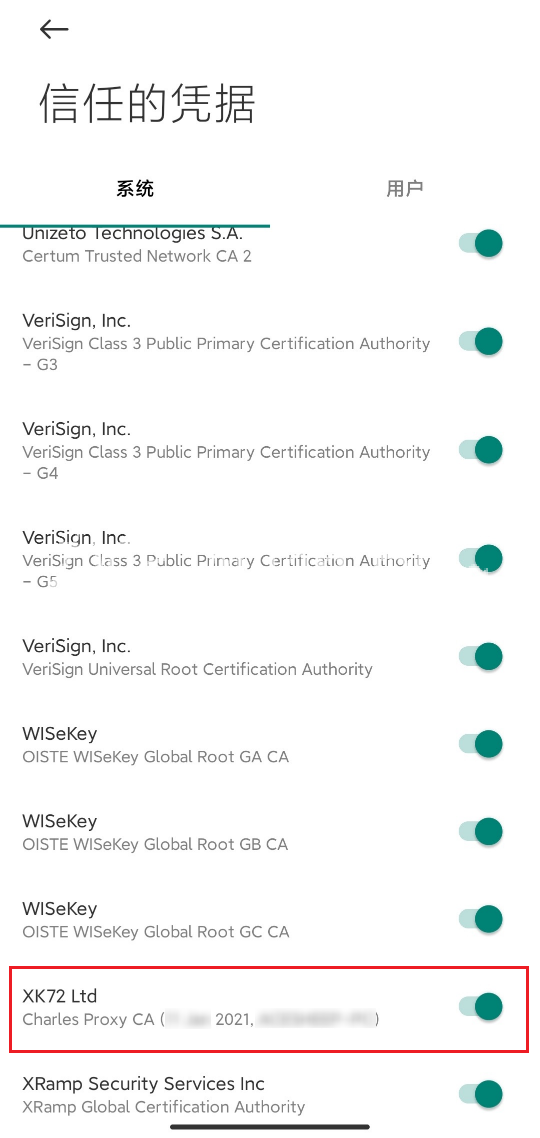
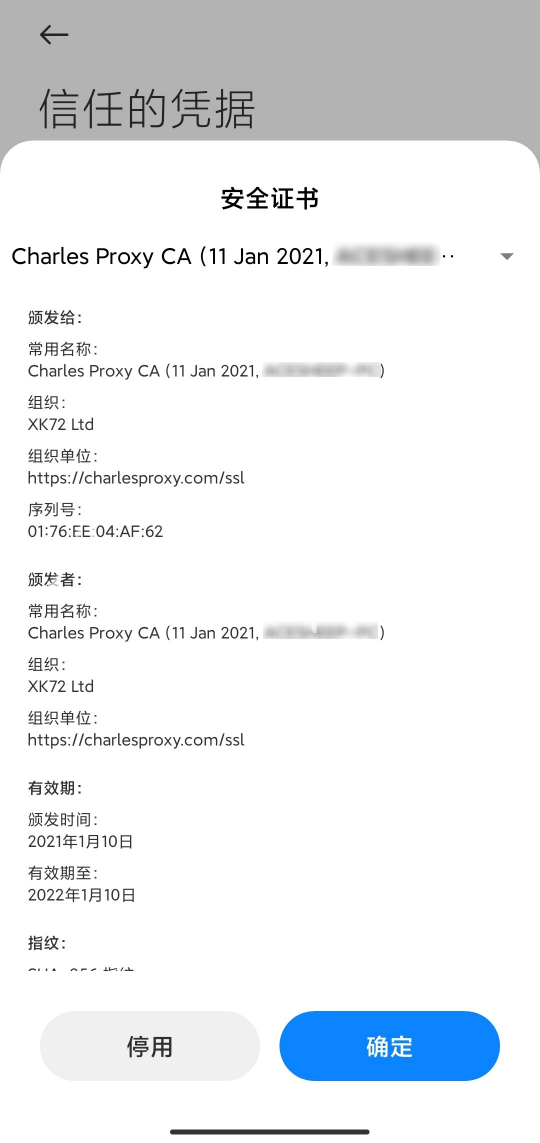
在手机中打开 系统设置 -> 安全 -> 更多安全设置 -> 加密与凭据 -> 信任的凭据, 在 “系统” 下找到刚才安装的证书 (本人用的 miui12 开发版, 不同手机位置可能不同)
原文